Meraki Security Appliance Webinar

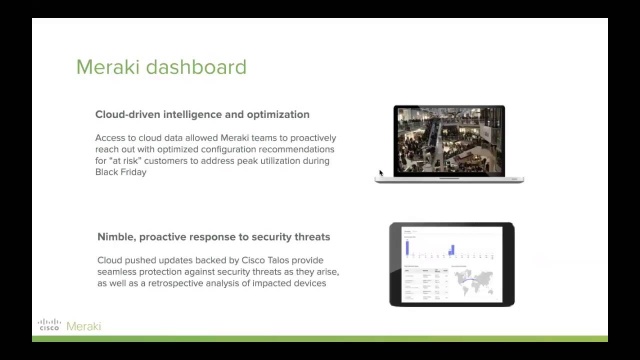
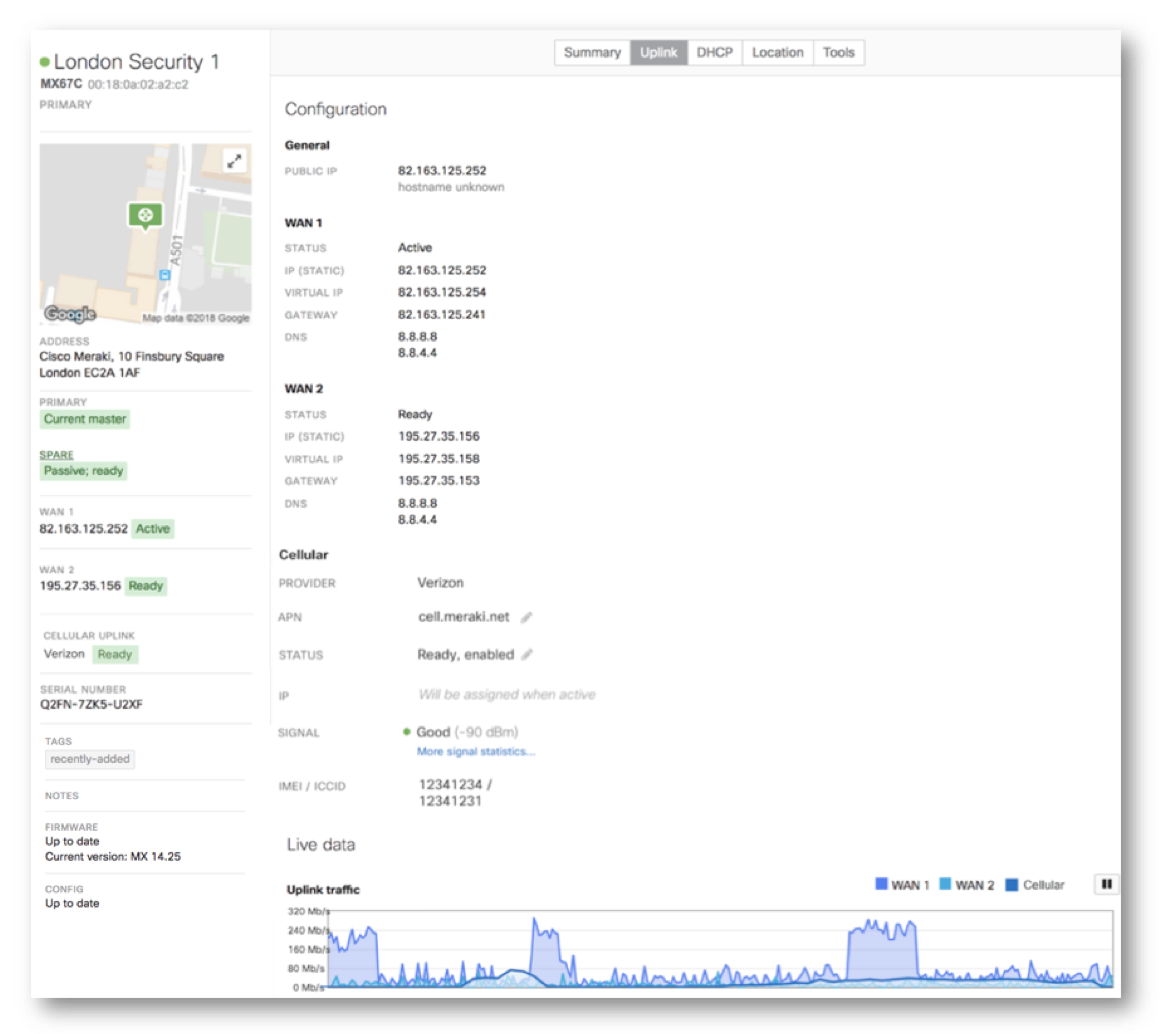
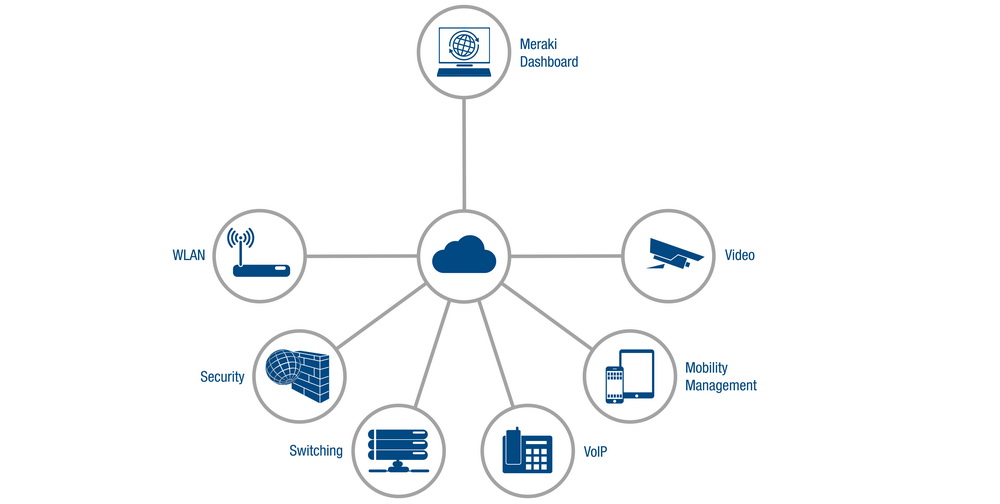
Cisco meraki security appliances can be remotely deployed in minutes using zero touch cloud provisioning.
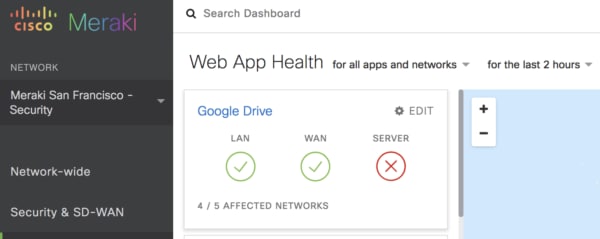
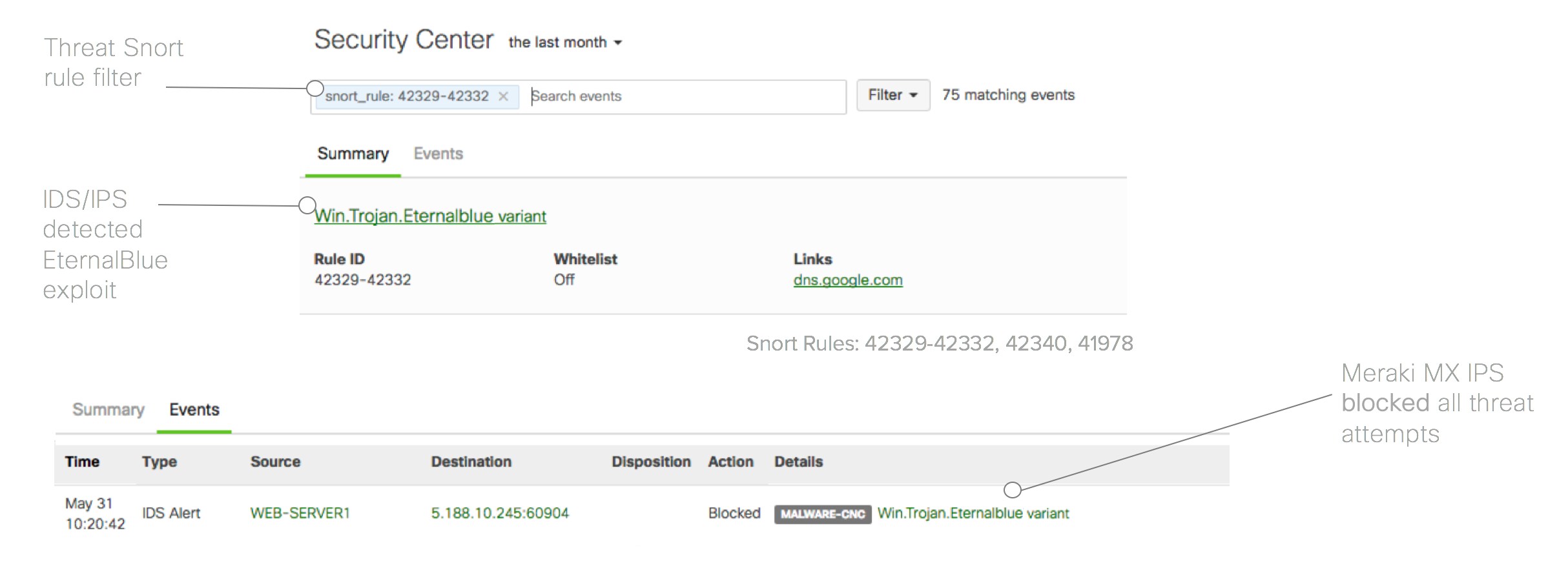
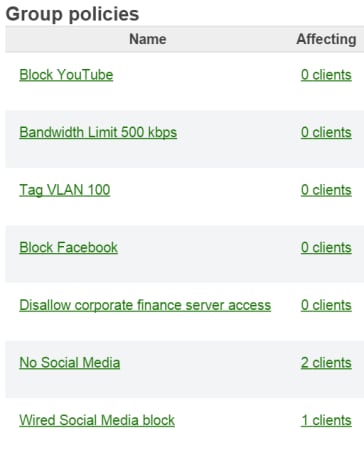
Meraki security appliance webinar. Security settings are simple to synchronize across thousands of sites using templates. If you attend a free meraki webinar about their next generation networking and firewall. Maximize the benefits of e rate with meraki cloud managed access points switches and security appliances that are easy to deploy configure and troubleshoot. We explore the security and sd wan features of the meraki mx platform and take a look at the product s full capabilities.
Healthcare ensure an optimal patient care experience with secure and reliable healthcare it solutions. Attend the live event live webinar or on demand webinar in its entirety. Learn how meraki security appliances can be remotely deployed in minutes using zero touch cloud provisioning and how sd wan capabilities in security appliances can reduce operational costs as well as improve resource usage for multi site deployments. Provide a valid company name and website.
After you complete the webinar they will ship the gear directly to your business and provide full tech support to get you set up. Simply take a brief cisco webinar explaining how the mx64 works and it s yours 1 800 value for free. Join us for a tour of this new class of cloud managed security appliance that integrates a next generation firewall internet gateway services site to site vpn and application traffic shaping. Delight your guests with 5 star service and insights by powering your business with meraki.
Meraki mx64w hw mx64w cloud managed security appliance with 802 11ac 1 962 30 1 035 95 inc gst 1 783 91 941 77 ex gst welcome to buy meraki everything cisco meraki cloud managed it solutions for faster smarter networking. While cisco meraki webinars are open to all audiences and while security appliances may be offered at live events to be eligible for a free security appliance participants must. Yes the appliance will continue to operate on the last known good configuration and enforce all configured security policies.