Network Load Balancer Health Check

By default every network security group includes the service tag azureloadbalancer to permit health probe traffic.
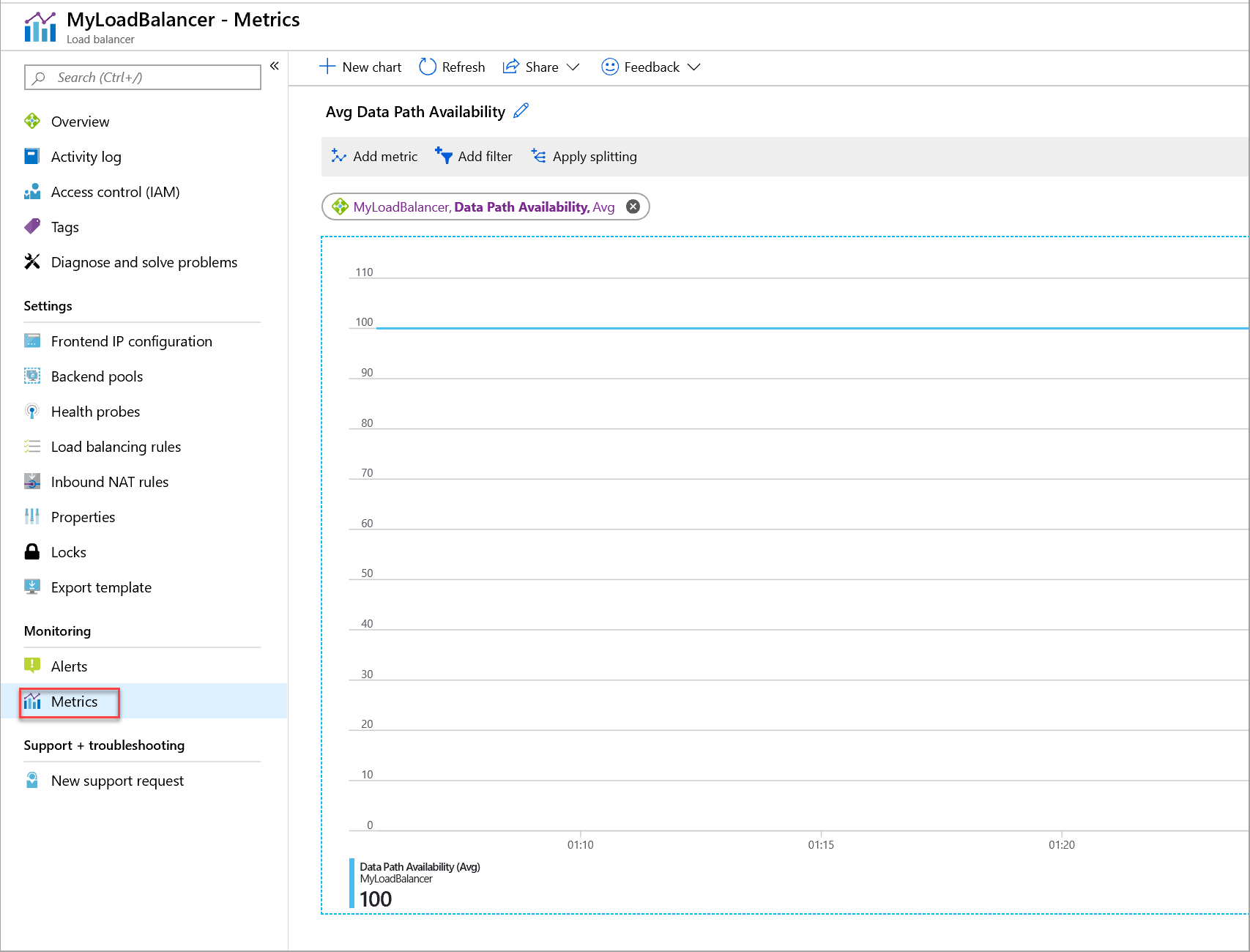
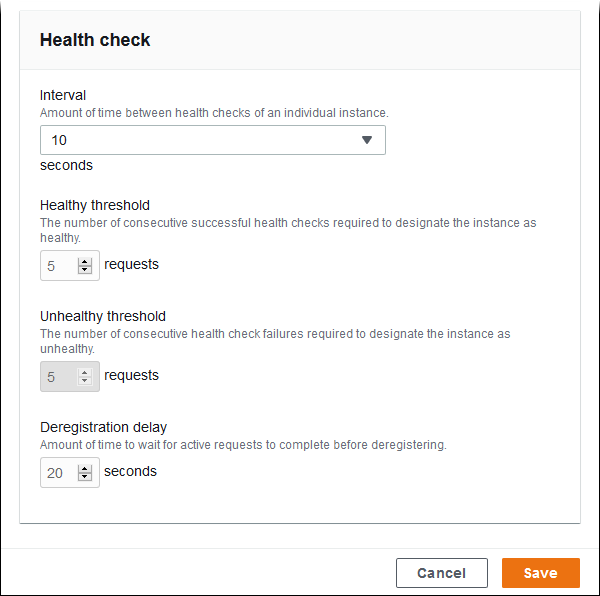
Network load balancer health check. For network load balancers you cannot set a custom value and the default is 10 seconds for tcp and https health checks and 6 seconds for http health checks. In addition to the ip ranges for health check probes your backends might also receive health check traffic from their metadata servers 169 254 169 254. If you enable cross zone load balancing each load balancer node routes requests to the healthy targets in all enabled availability zones. For example you can register instance ids ip addresses and lambda functions.
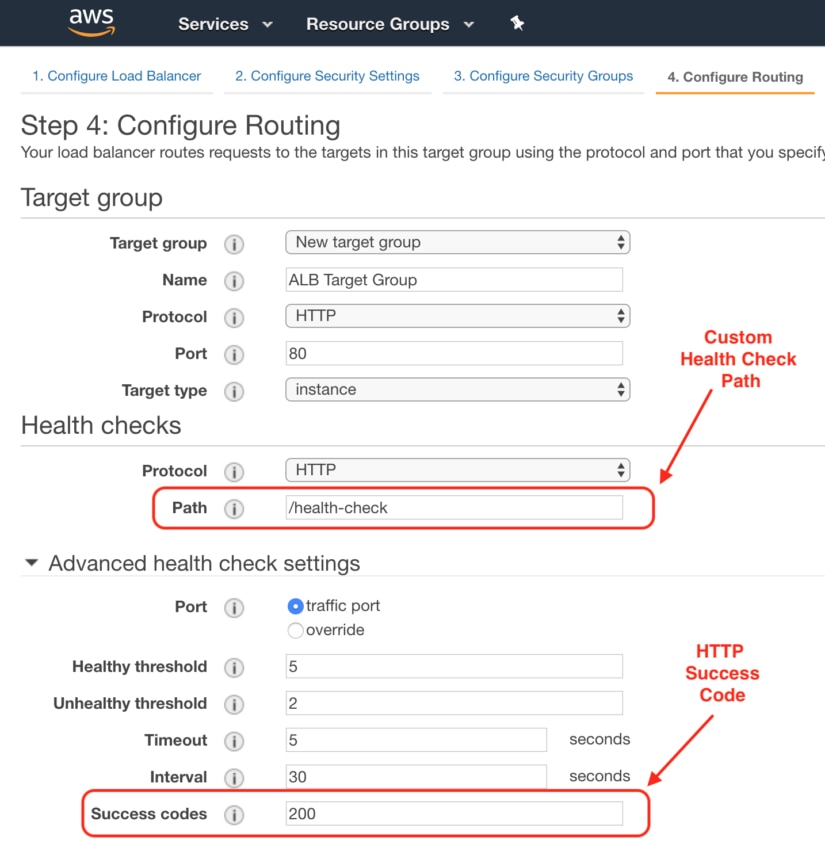
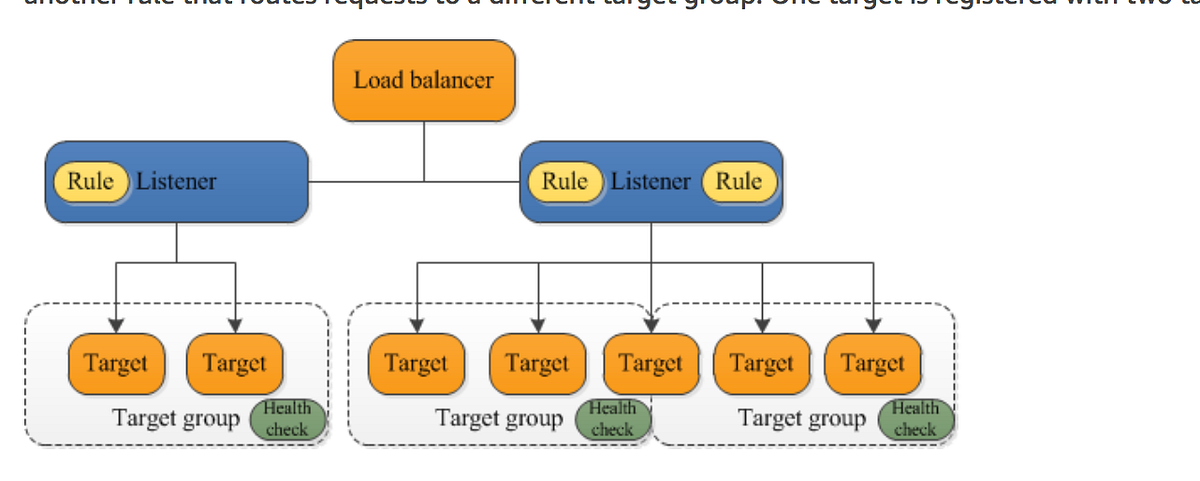
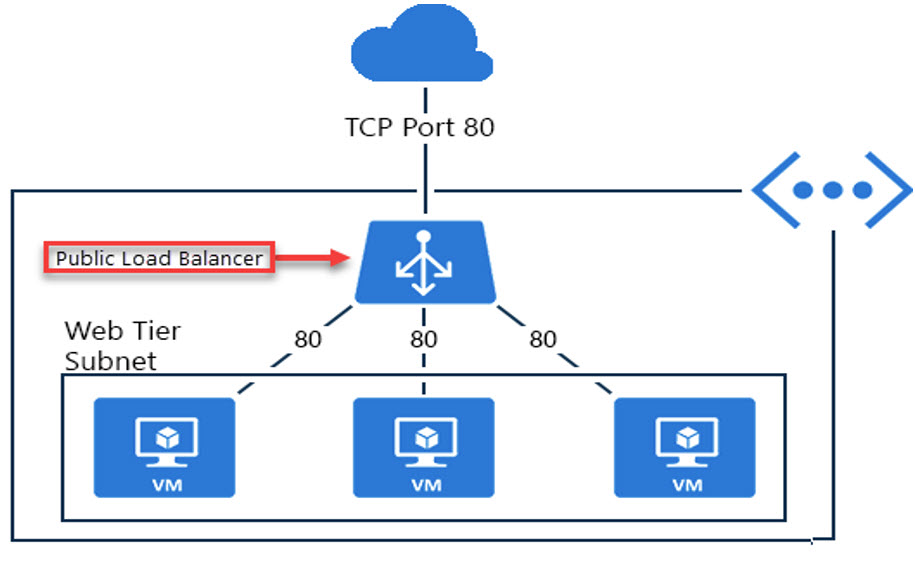
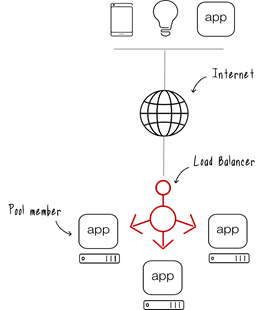
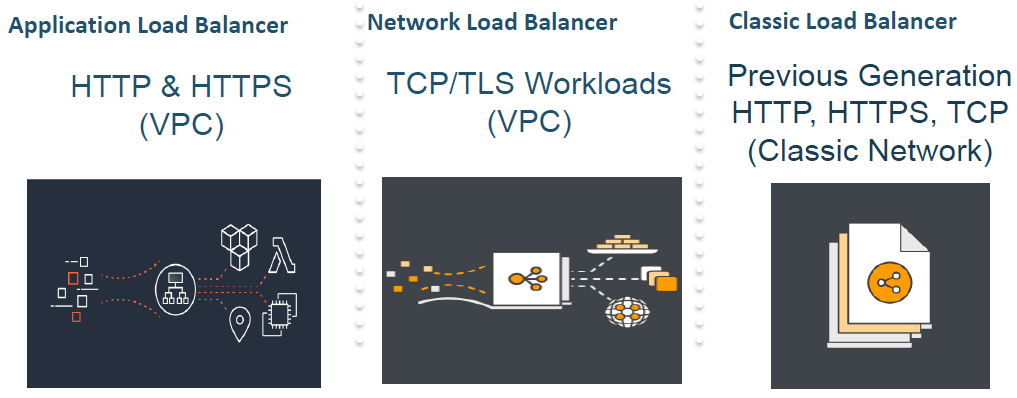
Network load balancers use active and passive health checks to determine whether a target is available to handle requests. When the load balancer sends an http get request to the health check path the application in your ecs container should return the default 200 ok response code. If you use an application load balancer you can update the matcher setting to a response code other than 200. An internal or private load balancer is used where private ips are needed at the frontend only.
Health checks for network load balancers are sent from these ip ranges. For http or https health check requests the host header contains the ip address of the load balancer node and the listener port not the ip address of the target and the health check port. Internal load balancers are used to load balance traffic inside a virtual network. It cannot use a legacy https health check or any modern health check.
If you are mapping incoming requests by host header you must ensure that health checks match any http host header. A network load balancer must use a legacy http health check. The target type of your target group determines which network interface that the load balancer sends health checks to on the targets. The http host header in the health check request contains the ip address of the load balancer node and the listener port not the ip address of the target and the health check port.
For more information see health checks for your target groups. A load balancer frontend can be accessed from an on premises network in a hybrid scenario. For load balancer s health probe to mark up your instance you must allow this ip address in any azure network security groups and local firewall policies. Healthy threshold optional the number of consecutive health checks successes required before considering an unhealthy target healthy.
You ll need to create ingress allow firewall rules that permit traffic from those ranges. If the target type is instance id then the load balancer sends health check requests to the primary network interface of the targets. If you use a network load balancer to balance tcp traffic you need to run an http service on the vms being load balanced so that they can respond to health check probes.