Network Mapping Tools Kali

Some of these tools can effectively be used during a pentest engagement to carry out vulnerability mapping across the three classes discussed above.
Network mapping tools kali. Creately available as downloadable software or as a cloud service this is a network map creation editor. Vulnerability scanning with kali linux. Kali linux contains a large amount of penetration testing tools from various different niches of the security and forensics fields. Kali linux installation guide for beginners part 1.
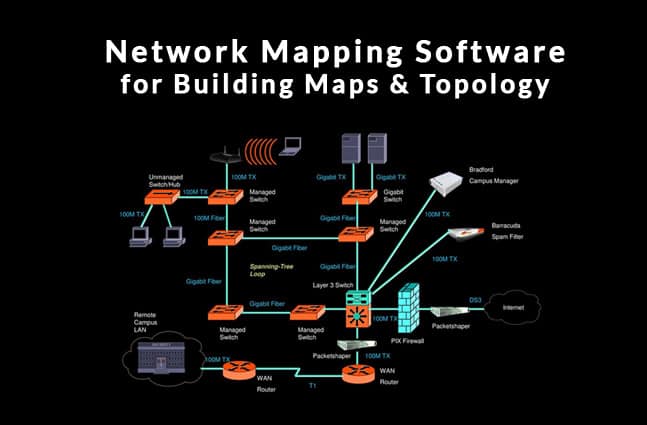
In addition the versions of the tools can be tracked against their upstream sources. For ease of reference we ll divide the most used software of kali linux into five distinct categories. 10 strike network diagram a network map creation editor that is supported by a network discovery module. The following tools will improve your documentation and presentation.
In addition to the combination of scanners and mapping tools there also exists complete network mapping solutions. Integrated network mapping solutions are clearly superior to the combination of network. Kali linux comes bundled with numerous tools for the penetration tester. This site aims to list them all and provide a quick reference to these tools.
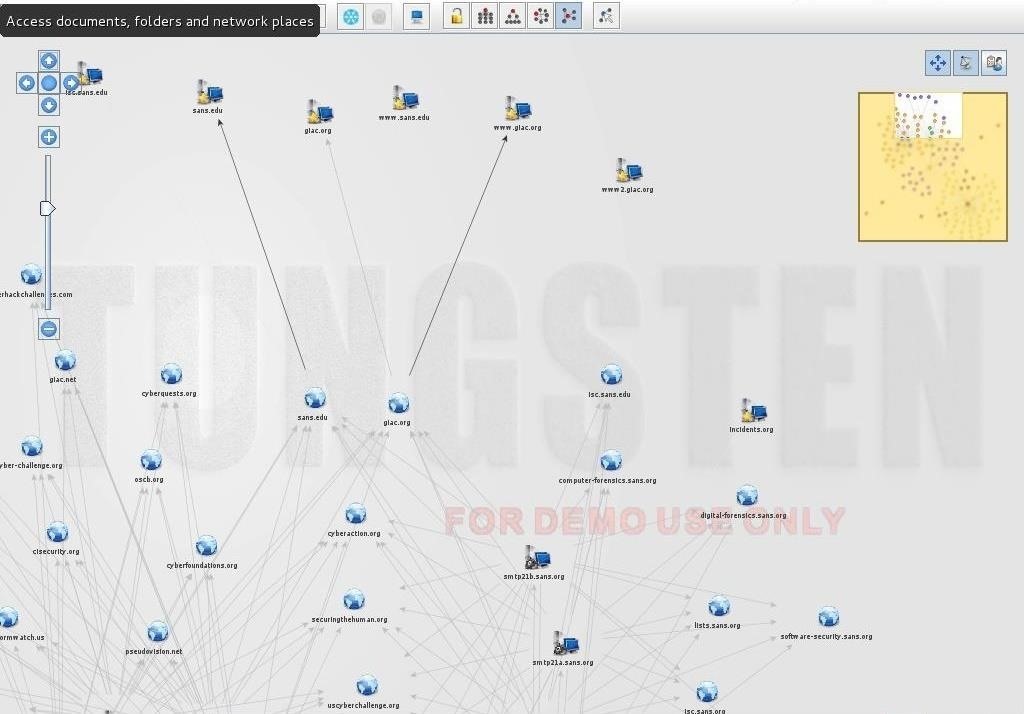
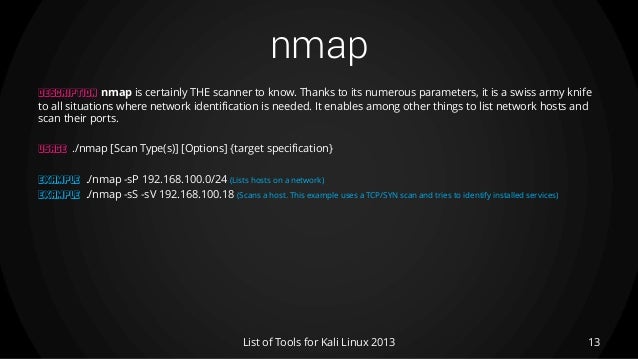
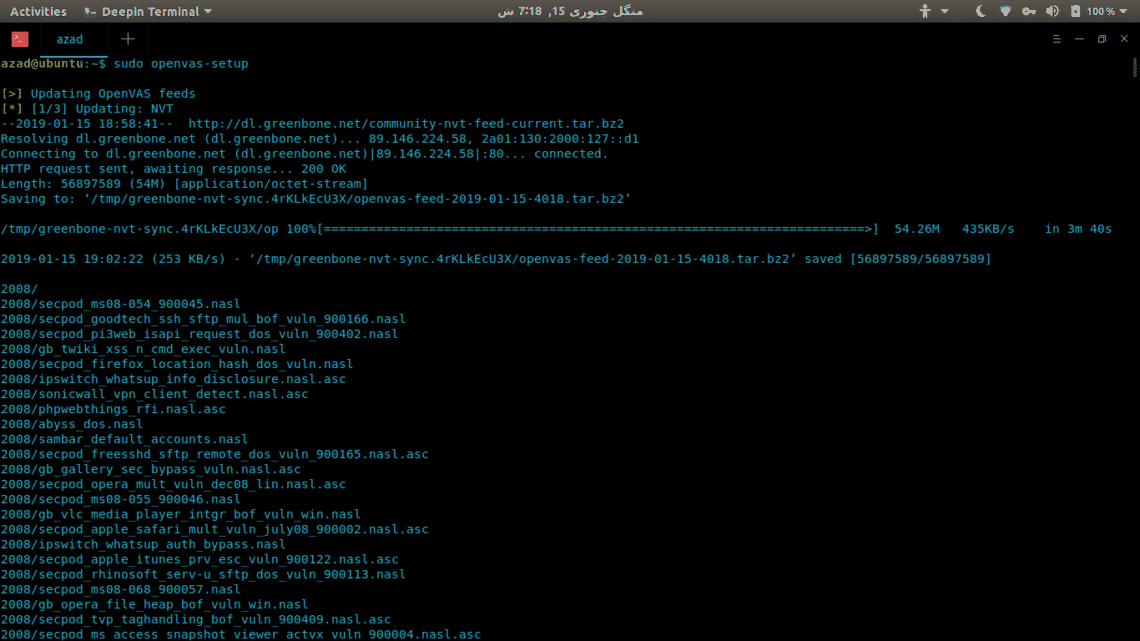
Mapping the network with the information gained from the earlier recipes we can now proceed to create the blueprint of the organization s network. Nmap is the world s most famous network mapper tool. The 25 most popular kali linux tools. Offsec services limited 2020 all rights reserved.
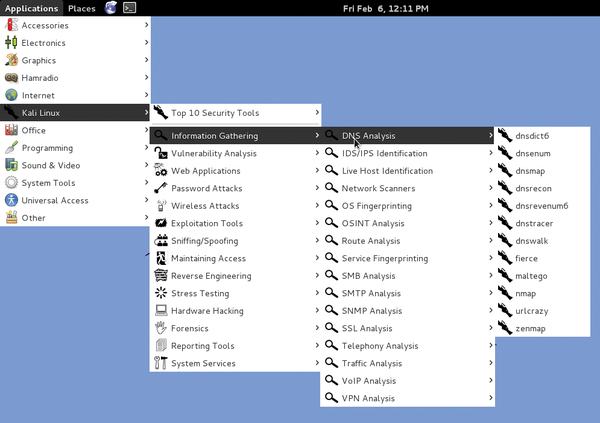
In other words to get insights about the host its ip address os detection and similar network security details like the number of open ports and what they are. The best network topology software and mapping tools. These scan the network and integrate the identified devices directly in network diagrams and maps so called auto mapping generating the network maps automatically. Information gathering vulnerability scanning wireless analysis tools password crackers exploitation tools and stress testing.
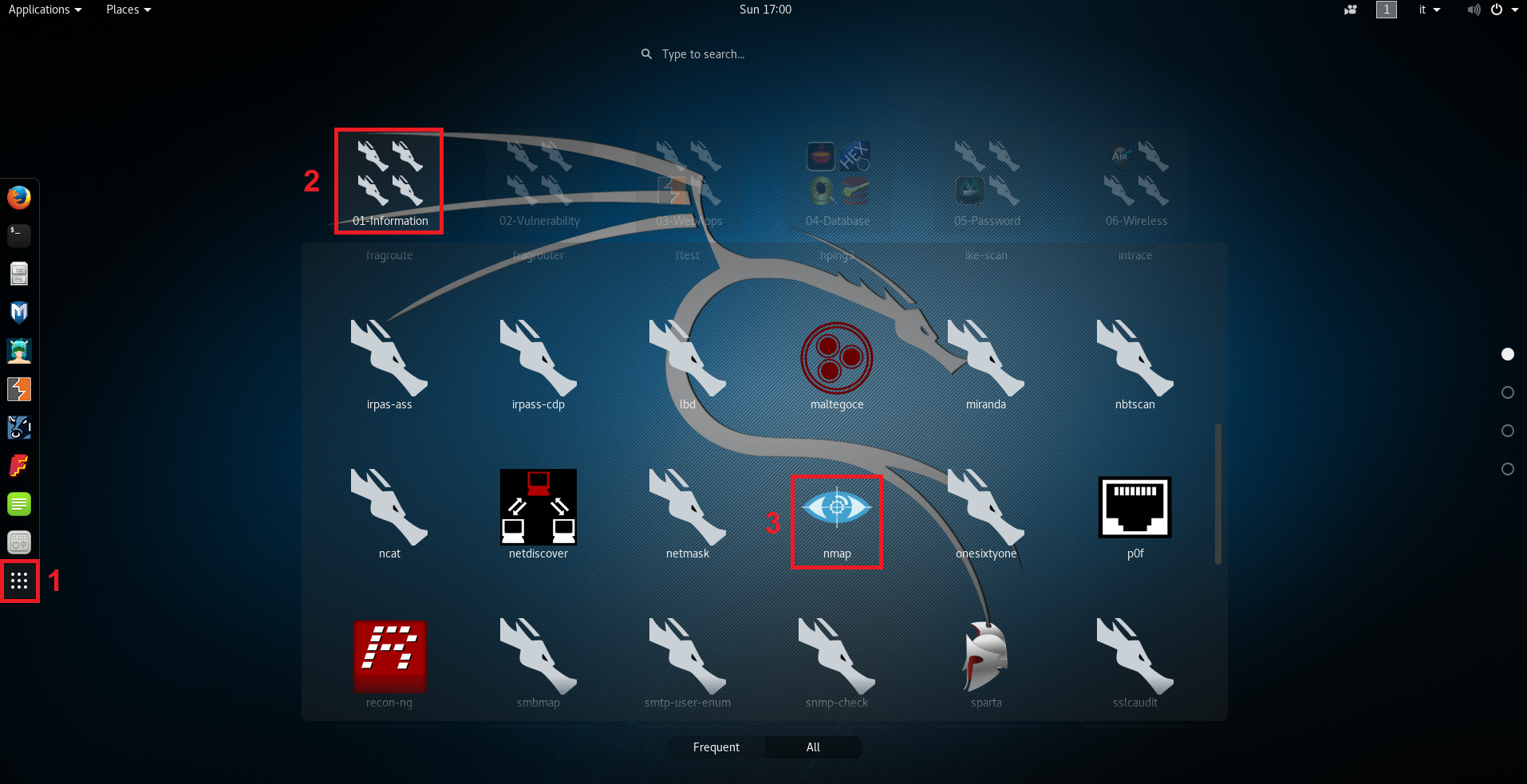
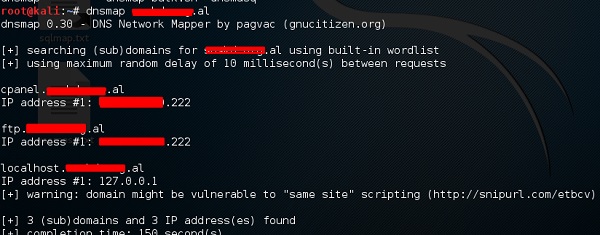
Nmap or network mapper is one of the most popular tools on kali linux for information gathering.